In cryptography, a brute force attack attempts to decipher encrypted content by guessing the encryption key. This attack is feasible when the encryption key is short, or if an attacker has sufficient information to try and guess the key.
When it comes to web forms, attackers do not have much time to guess a key. Google or Facebook will only let somebody try to log into your account so many times before they “lock it down.”
When hackers obtain the internal database of a company, however, they have all the time in the world to guess your password—even if it’s encrypted.
Websites should salt and hash passwords to protect users
When websites store your passwords, they should (but don’t always) salt and hash the user passwords, so that somebody in possession of the user database can’t use it.
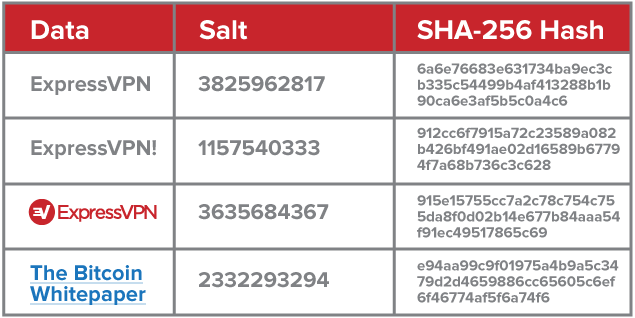
Hash functions, such as SHA-256, are one-way cryptographic functions. Any piece of data, text, image, or number can be “hashed,” and no matter how long the input is, the result will always be 256 bits in length. When encoded in hexadecimal (like below), this results in a 64-character string.
How attackers crack your password
To make things difficult for potential hackers, websites will amend passwords with a “salt,” which is a random piece of data (see how salting and hashing works).
Computing a hash from the text, a picture or file is trivial and will not take a computer any considerable amount of time or resources. But if all you know is the hash, the only way to find out the original value is a brute-force attack. This is why a hashing function is also called one-way encryption. It is easy to go from text to the hash, but very hard to go the other way.
Password crackers in possession of a stolen user database might see the list of usernames, the salt value for each user, and the hash.
With these details, they can attempt to guess the passwords of each user, salt and hash them, and check their result against the hash stored in the database. If the hash matches, they know they have found the password.
An attacker must input the username and password exactly, as changing the hash even just a tiny bit (as seen above) will result in a completely different hash.
How many password combinations are there?
Assuming a password only consists of lowercase letters, for each character there are 26 possibilities. Therefore, you would expect to be able to guess a one-character password within 13 attempts.
A two-character password has 26×26 options and would take (26×26)/2 attempts to decipher.
The formula c=(m^n)/2 describes the relationship between the possibilities for each character (m), the password length (n) and the expected number of guesses (c).
The relationship between the password length and the number of guesses to crack it
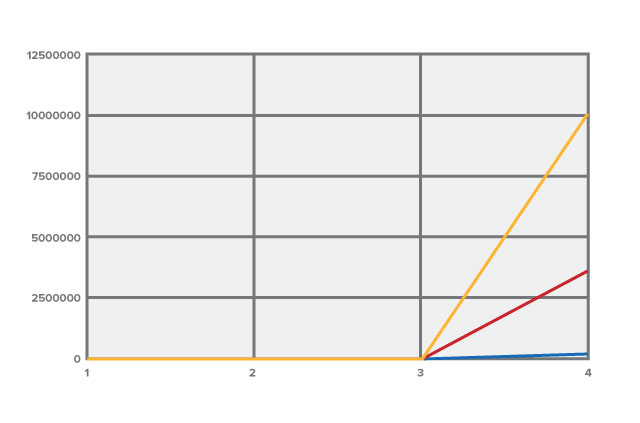
- Lowercase passwords (m=26)
- Uppercase and lowercase (m=52)
- Upper and lowercase and special characters (m=67)
While both complexity and length contribute to a password’s strength, it is far more valuable to add a character than to increase its complexity.
Adding an extra character to a four-character password, using only lowercase characters, makes it 26 times more difficult to crack, whereas doubling the possible characters to 52 (i.e., adding uppercase characters) only makes it 16 times more difficult to crack.
The logarithmic scale makes the relationship between password length and required guesses to crack more apparent
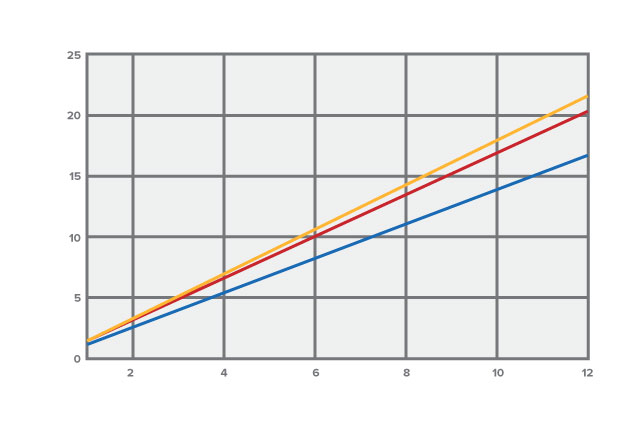
- Lowercase passwords (m=26)
- Uppercase and lowercase (m=52)
- Upper and lowercase and special characters (m=67)
How long does it take to crack a password?
How quickly an attacker can crack your password depends on how fast the attacker’s computer hardware is.
A regular computer would likely make about 100,000 guesses per second. A dedicated GPU could be 100 times faster than this, and it’s possible to create a password cracking farm with hundreds of GPUs.
If we assume the attacker has a regular computer, capable of 100,000 guesses per second, any lowercase password with less than six characters will take less than one minute to crack.
But the solve-time increases exponentially, and an eight-character password would take 12 days to crack. A 12-character password would take over 12,000 years.
Whether a 12-character password is enough depends on the value of what it protects and the scale of the attack. If attackers are only after a single target, a 12-character password might be within their reach.
It’s crucial, then, to protect valuable data (such as personal information or Bitcoin private keys) with far longer passwords. When encrypting your Bitcoin wallet, for example, a key of over 32 characters might be a good idea.
The more information an attacker has, the faster a crack will happen
The above calculations assume that the attacker does not know anything about the password, other than whether it includes uppercase or lowercase characters.
In reality, the attacker might have some guesses. From previous decrypted password lists we know what the most common passwords are. If there is no specific target, an attacker could check common passwords with an email list relatively quickly.
People also tend to choose passwords that only have numbers at the end (such as hello111), and include the name of the service or URL somewhere. A password used for Gmail that contains the words google or gmail and has four digits at the end (such as gmailpanther1234), is easy to crack, even if it is long.
People also tend to use names of their pets or children as passwords, sometimes in combination with birth dates or years, making their password easier to guess than people might think.
Use strong passwords with password managers
The most important rule is: Always use a strong password.
To avoid the hassle of making up and remembering so many robust passwords, use a random password generator to conveniently create long, unique, and truly unguessable passwords.
If you then store those passwords with a password manager (such as our partner LastPass), you will only need to remember a single password (which you could generate with Diceware, to make it extra secure). In addition, two-factor authentication helps protect accounts against even more sophisticated attacks, such as passwords obtained through phishing attacks.




























Comments
fDrt(xg8pgYl{wN~n
I need to reference your for an assignment, what is your last name?
I’m very flattered! My name is Lexie M. Having only one letter in my last name can be quite an inconvenience…
Oky…